Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 22 outubro 2024
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Learn ethical hacking (@learn_hacking4) • Instagram photos and videos
Ronin Hack: North Korea's Lazarus Behind $540 Million Axe Infinity Breach

Understanding Linux Privilege Escalation: Tips to Improve Cy

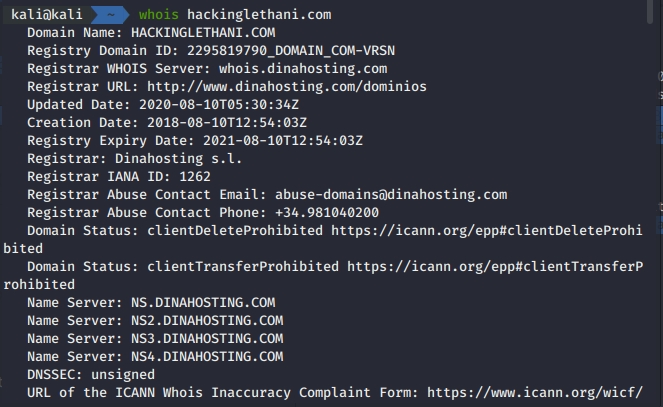
Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)

Should you use Let's Encrypt for internal hostnames? – Terence Eden's Blog
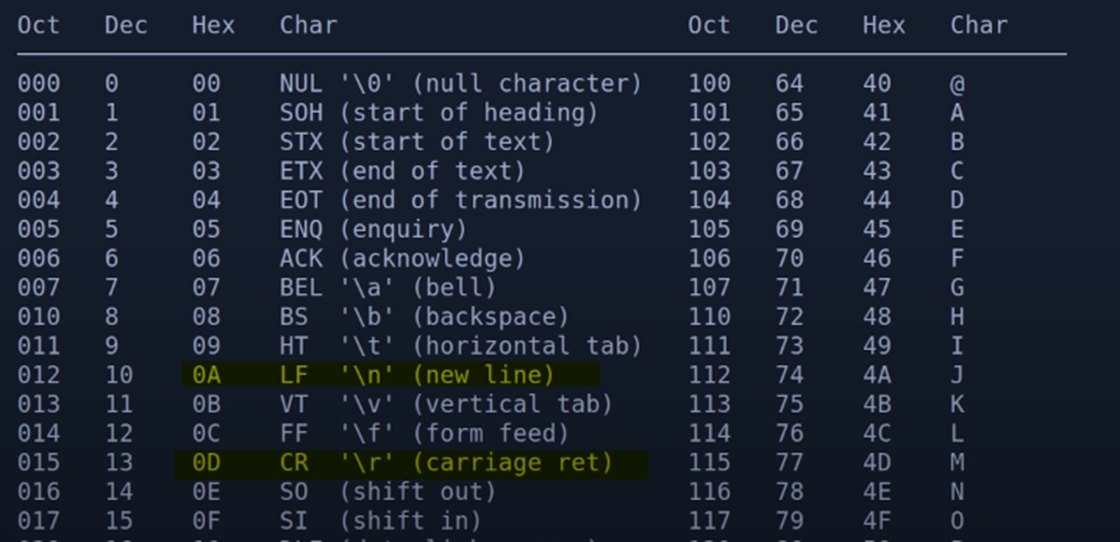
Infrastructure Hacking: Telnet Protocol » Hacking Lethani
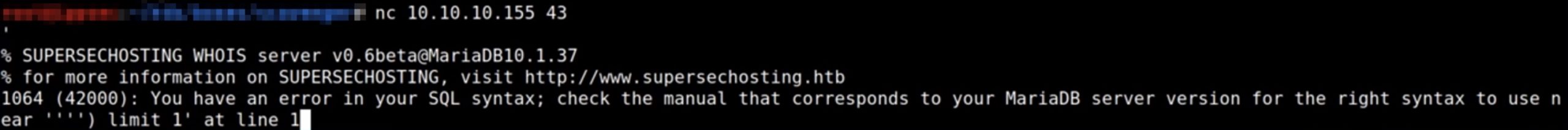
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Whois Lookup Ethical Hacking

Tips for Investigating Cybercrime Infrastructure

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS
Ethical Hacking - How to start
Recomendado para você
-
 A Complete Guide to WHOIS Lookup22 outubro 2024
A Complete Guide to WHOIS Lookup22 outubro 2024 -
 Use WHOIS Lookup to Know Who Owns A Domain22 outubro 2024
Use WHOIS Lookup to Know Who Owns A Domain22 outubro 2024 -
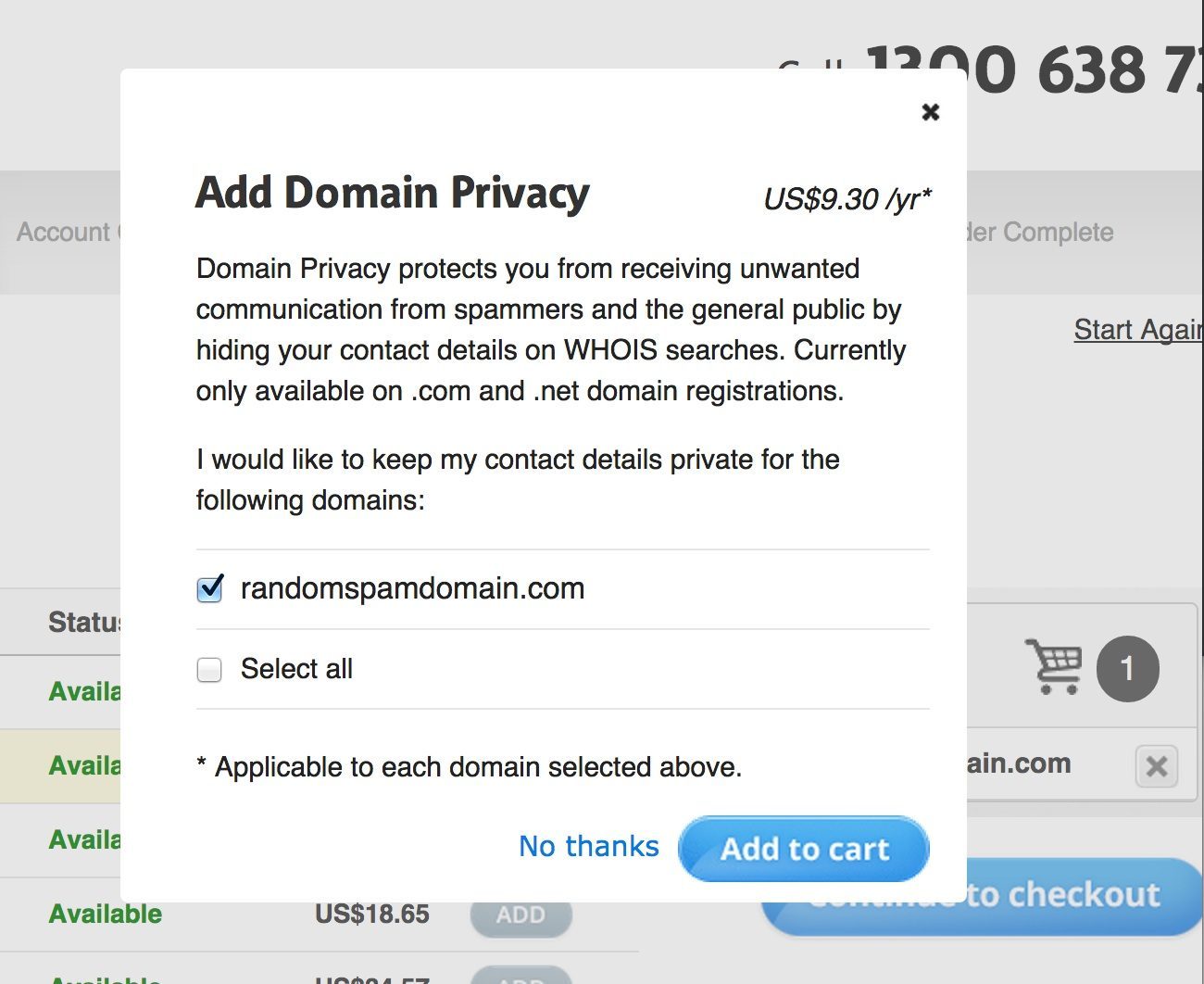 WHOIS Email, Email Address WHOIS22 outubro 2024
WHOIS Email, Email Address WHOIS22 outubro 2024 -
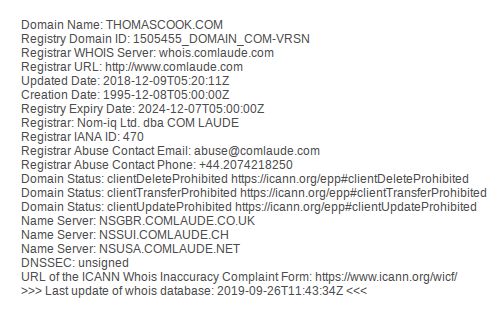 Nixintel Open Source Intelligence & Investigations Search Tip22 outubro 2024
Nixintel Open Source Intelligence & Investigations Search Tip22 outubro 2024 -
 Domain whois State / Country not private - Registrar - Cloudflare22 outubro 2024
Domain whois State / Country not private - Registrar - Cloudflare22 outubro 2024 -
WHOIS/Domain Expiry Check Basics – Uptime.com22 outubro 2024
-
 What is: WHOIS Lookup22 outubro 2024
What is: WHOIS Lookup22 outubro 2024 -
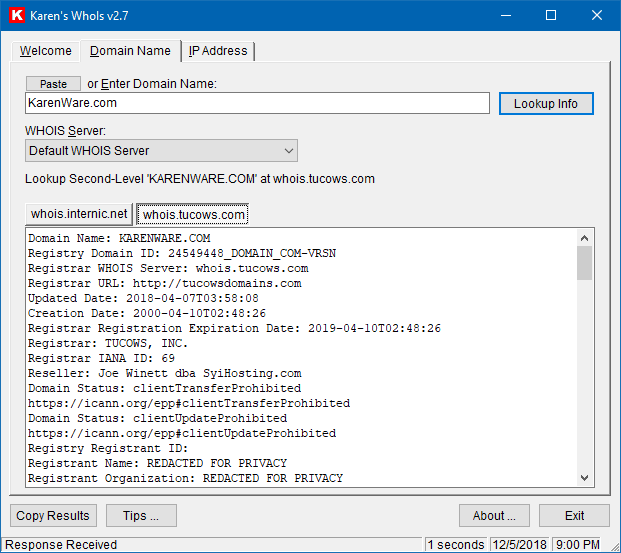 WhoIs v2.7, Karen's Power Tools22 outubro 2024
WhoIs v2.7, Karen's Power Tools22 outubro 2024 -
Whois Icon22 outubro 2024
-
WhoIs - Apps on Google Play22 outubro 2024
você pode gostar
-
 Dr. Collingwood, NewScapePro Wiki22 outubro 2024
Dr. Collingwood, NewScapePro Wiki22 outubro 2024 -
 Enquete A Fazenda 15: Jaquelline, Nadja, WL e Márcia perdem prova22 outubro 2024
Enquete A Fazenda 15: Jaquelline, Nadja, WL e Márcia perdem prova22 outubro 2024 -
 Kit Cubo Mágico Profissional 2x2, 3x3,brinquedo Piramix - Jmix - Cubo Mágico - Magazine Luiza22 outubro 2024
Kit Cubo Mágico Profissional 2x2, 3x3,brinquedo Piramix - Jmix - Cubo Mágico - Magazine Luiza22 outubro 2024 -
 Bolo em chantininho no tema: Chapeuzinho Vermelho ❣️ #bolochapeuzinho… Bolo da chapeuzinho vermelho, Festa da chapeuzinho vermelho, Decoraçao chapeuzinho vermelho22 outubro 2024
Bolo em chantininho no tema: Chapeuzinho Vermelho ❣️ #bolochapeuzinho… Bolo da chapeuzinho vermelho, Festa da chapeuzinho vermelho, Decoraçao chapeuzinho vermelho22 outubro 2024 -
 Football Legends 2019 🔥 Play online22 outubro 2024
Football Legends 2019 🔥 Play online22 outubro 2024 -
 Black Summoner ANIME TRAILER22 outubro 2024
Black Summoner ANIME TRAILER22 outubro 2024 -
 Bologna x Cesena: saiba onde assistir ao vivo ao jogo (11/08)22 outubro 2024
Bologna x Cesena: saiba onde assistir ao vivo ao jogo (11/08)22 outubro 2024 -
 Van Crombrugge :: Genk :: Perfil do Jogador22 outubro 2024
Van Crombrugge :: Genk :: Perfil do Jogador22 outubro 2024 -
Master, Grandmaster, and Challenger: The Apex Tiers – League of Legends Support22 outubro 2024
-
 Baixar Piano Tiles 2 para telefones22 outubro 2024
Baixar Piano Tiles 2 para telefones22 outubro 2024