Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 24 outubro 2024

Describing activities of a crime group attacking Ukraine.
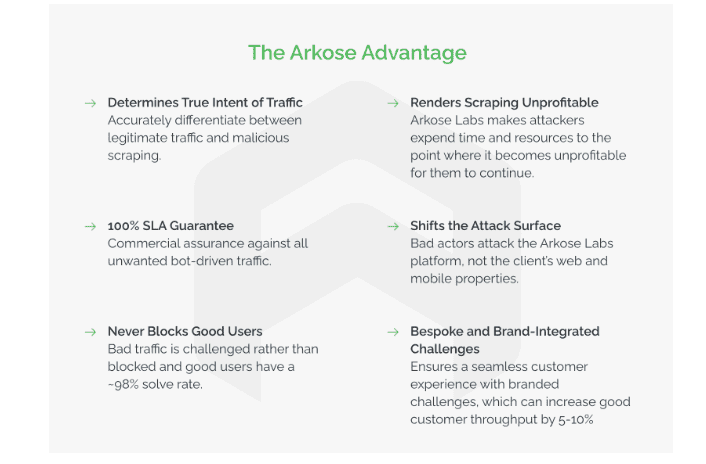
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Balancing act: countering digital disinformation while respecting freedom of expression: Broadband Commission research report on 'Freedom of Expression and Addressing Disinformation on the Internet

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense

Disk-Locking HDDCryptor/Mamba Ransomware Makes a Comeback - Security News - Trend Micro IN
Full article: From cold to cyber warriors: the origins and expansion of NSA's Tailored Access Operations (TAO) to Shadow Brokers

Security in product lifecycle of IoT devices: A survey - ScienceDirect

424B4
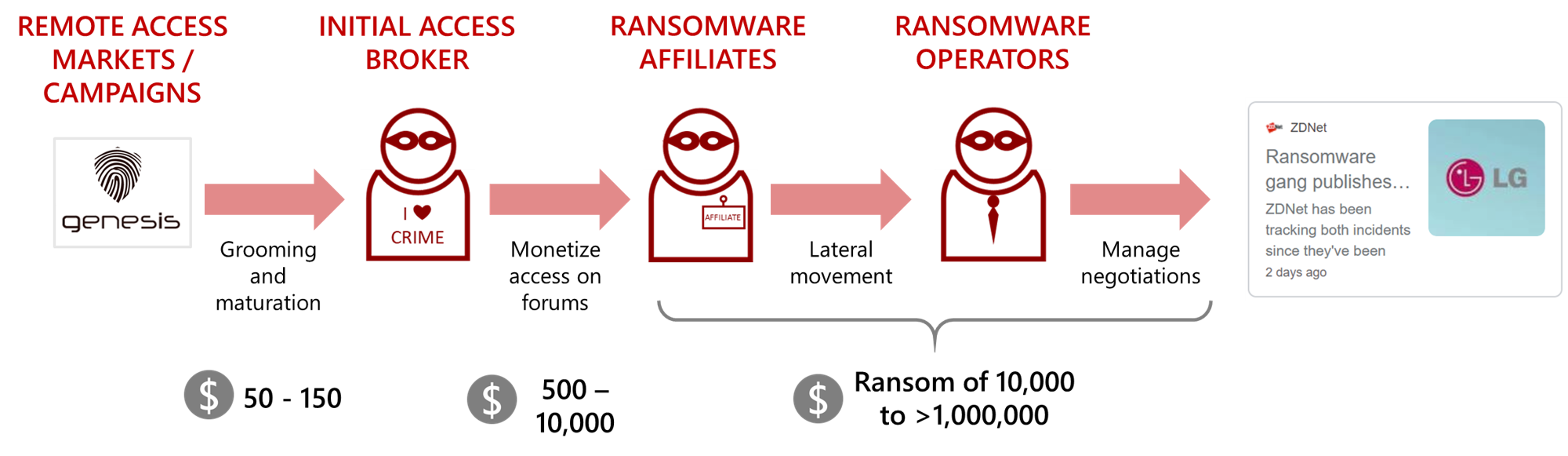
The Secret Life of an Initial Access Broker • KELA Cyber Threat Intelligence
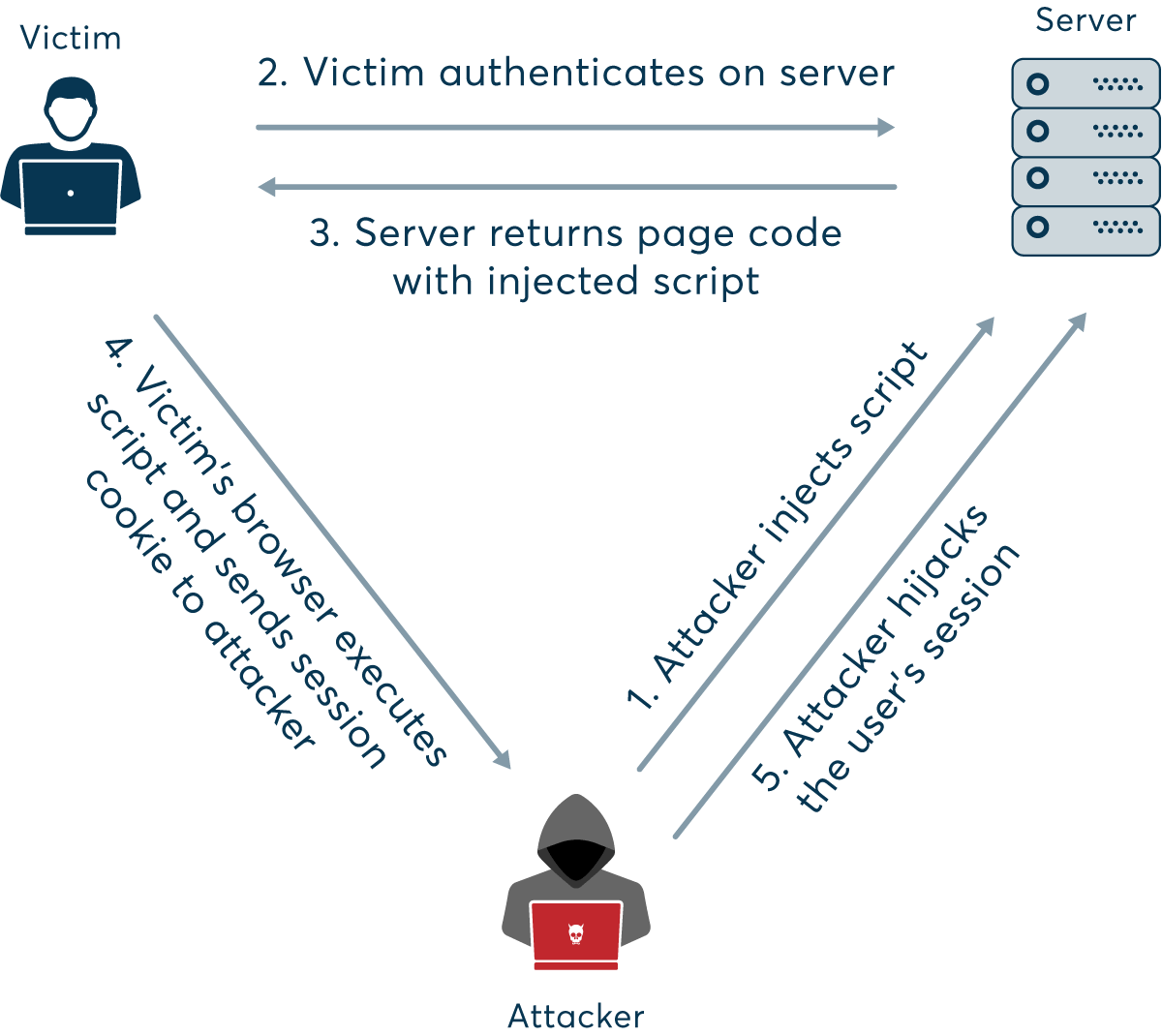
What Is Session Hijacking?
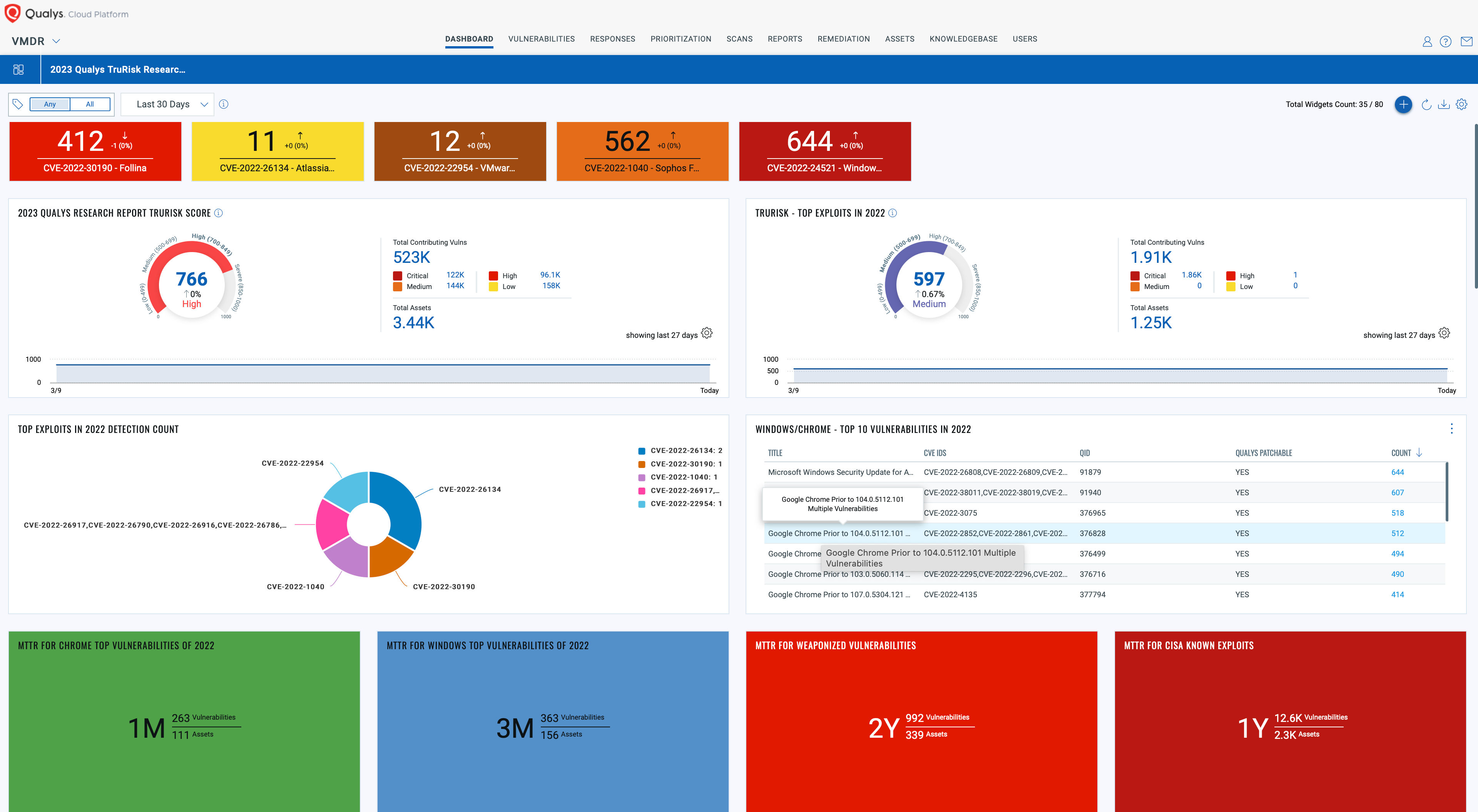
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Security in product lifecycle of IoT devices: A survey - ScienceDirect

US7236486B2 - Integrated customer web station for web based call management - Google Patents

What Is a Brute Force Attack? Types and Preventions in 2022 - Spiceworks
New Report: Risky Analysis: Assessing and Improving AI Governance Tools
Recomendado para você
-
Analysis Group24 outubro 2024
-
 Analysis Group Office Renovation and Restack24 outubro 2024
Analysis Group Office Renovation and Restack24 outubro 2024 -
 Analysis Group - P&R Desjardins24 outubro 2024
Analysis Group - P&R Desjardins24 outubro 2024 -
 About - Analysis Group24 outubro 2024
About - Analysis Group24 outubro 2024 -
 Joint Pharmaceutical Analysis Group (joint with RPS)24 outubro 2024
Joint Pharmaceutical Analysis Group (joint with RPS)24 outubro 2024 -
 Protein Analysis Group – University of Copenhagen24 outubro 2024
Protein Analysis Group – University of Copenhagen24 outubro 2024 -
 Groupe d'analyse – Montréal - Analysis Group24 outubro 2024
Groupe d'analyse – Montréal - Analysis Group24 outubro 2024 -
HKUST Case Analysis Team24 outubro 2024
-
Venus Exploration Analysis Group (VEXAG) (@unveilvenus) / X24 outubro 2024
-
 Home - AMAG Inc.24 outubro 2024
Home - AMAG Inc.24 outubro 2024
você pode gostar
-
 Narutop99 results so far: Top 10 characters, according to polls24 outubro 2024
Narutop99 results so far: Top 10 characters, according to polls24 outubro 2024 -
 TABELA DO CAMPEONATO PAULISTA 202224 outubro 2024
TABELA DO CAMPEONATO PAULISTA 202224 outubro 2024 -
 Young Nudy - Peaches & Eggplants Remix(Feat.21 Savage,Sexyy Red,Dababy,Latto)24 outubro 2024
Young Nudy - Peaches & Eggplants Remix(Feat.21 Savage,Sexyy Red,Dababy,Latto)24 outubro 2024 -
 111 desenhos do Naruto para colorir24 outubro 2024
111 desenhos do Naruto para colorir24 outubro 2024 -
 Trollhunter Jim in the Darklands, an art print by shamidraws - INPRNT24 outubro 2024
Trollhunter Jim in the Darklands, an art print by shamidraws - INPRNT24 outubro 2024 -
 Roblox's contrast of over 100 million monthly users - Techrecipe24 outubro 2024
Roblox's contrast of over 100 million monthly users - Techrecipe24 outubro 2024 -
 Ashfur Warrior cats art, Warrior cats fan art, Warrior cat drawings24 outubro 2024
Ashfur Warrior cats art, Warrior cats fan art, Warrior cat drawings24 outubro 2024 -
Pokémon Go Kerala, Got the mythical Pokemon zarude🤩👌24 outubro 2024
-
/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2021/d/z/FtaKW4TXGTvda1F1PIOA/d733ae80-c8a8-47f3-b206-a031d25b3c16.jpg) Brasil x Venezuela: escalações, desfalques e arbitragem do jogo da Copa América, copa américa24 outubro 2024
Brasil x Venezuela: escalações, desfalques e arbitragem do jogo da Copa América, copa américa24 outubro 2024 -
 Caderno de receitas da Lara Jean em 2023 Receitas, Caderno de receitas, Netflix filmes e series24 outubro 2024
Caderno de receitas da Lara Jean em 2023 Receitas, Caderno de receitas, Netflix filmes e series24 outubro 2024



